Radius Server Port Number Guide
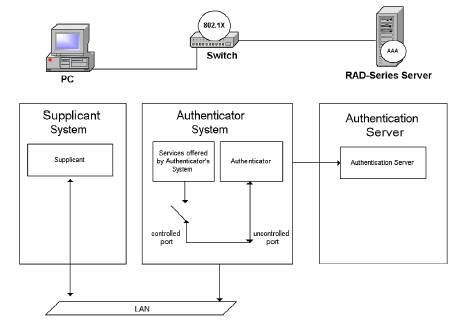
The Radius server port number is a critical component in the configuration and operation of Radius (Remote Authentication Dial-In User Service) protocols. Radius is a widely used protocol for authentication, authorization, and accounting (AAA) in network environments, particularly in scenarios where remote access is required, such as VPN connections, wireless networks, and dial-up connections. Understanding the port numbers used by Radius is essential for network administrators to ensure secure, efficient, and reliable network operations.
Introduction to Radius Server Port Numbers

Radius operates on two primary ports: 1812 for authentication and 1813 for accounting. These ports are standardized by the Internet Engineering Task Force (IETF) and are used by Radius servers and clients to communicate. The authentication port (1812) is used for exchanging authentication and authorization messages, while the accounting port (1813) is used for sending accounting information, such as user session start, stop, and update messages.
Radius Authentication Port (1812)
The Radius authentication port, 1812, is used by the Network Access Server (NAS) to send user credentials to the Radius server for verification. When a user attempts to access the network, the NAS sends an Access-Request packet to the Radius server on port 1812. The Radius server then processes the request, checks the user’s credentials against its database or an external database like Active Directory, and responds with an Access-Accept or Access-Reject packet. The use of a standardized port like 1812 simplifies the configuration process for network administrators and ensures interoperability between different vendors’ equipment.
Radius Accounting Port (1813)
The Radius accounting port, 1813, is utilized by the NAS to send accounting information to the Radius server. This information can include details about the user’s session, such as start and stop times, the amount of data transferred, and any errors that occurred. The accounting data is essential for billing purposes, network usage tracking, and security audits. By using port 1813 for accounting, network administrators can ensure that this critical information is accurately collected and stored for future reference or analysis.
| Radius Port Number | Description |
|---|---|
| 1812 | Authentication |
| 1813 | Accounting |
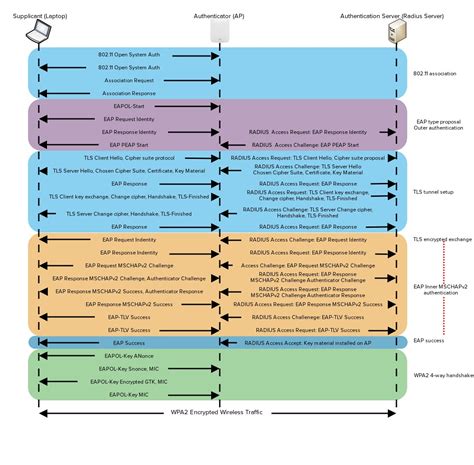
Configuring Radius Server Port Numbers
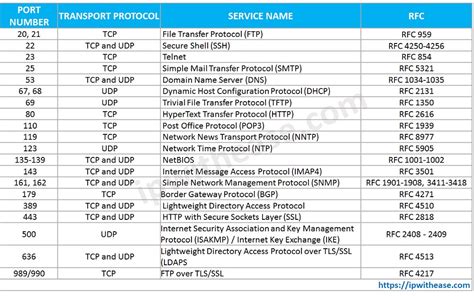
Configuring the Radius server to use the correct port numbers is a straightforward process. Most Radius server software and appliances come with default settings that use ports 1812 and 1813 for authentication and accounting, respectively. However, network administrators may need to manually configure these settings in certain scenarios, such as when using non-standard ports for specific applications or when integrating the Radius server with other network devices that require custom configurations.
Best Practices for Radius Port Configuration
When configuring Radius server port numbers, it’s essential to follow best practices to ensure security and reliability. This includes using secure protocols for communication, regularly updating the Radius server software to patch security vulnerabilities, and monitoring network traffic for any suspicious activity related to Radius ports. Additionally, configuring firewalls to allow traffic only on necessary ports and implementing rate limiting can help prevent denial-of-service (DoS) attacks targeting the Radius server.
Key Points
- Radius uses ports 1812 for authentication and 1813 for accounting.
- Understanding and correctly configuring these ports is crucial for network security and functionality.
- Following best practices, such as using secure protocols and monitoring network traffic, can enhance the security of Radius operations.
- Regular software updates and firewall configuration are essential for preventing security breaches.
- Considering alternative protocols like Diameter for future implementations can offer improved security and functionality.
Conclusion and Future Directions
In conclusion, the Radius server port numbers, particularly 1812 and 1813, play a vital role in the authentication, authorization, and accounting processes in network environments. As network technologies evolve and security concerns become more pronounced, understanding and properly configuring these ports will remain essential for network administrators. Looking ahead, the adoption of more secure and feature-rich protocols like Diameter will likely become more prevalent, offering enhanced security and better support for modern network authentication requirements.
What is the primary purpose of the Radius authentication port 1812?
+The primary purpose of the Radius authentication port 1812 is to facilitate the exchange of authentication and authorization messages between the Network Access Server (NAS) and the Radius server.
How does the Radius accounting port 1813 contribute to network management?
+The Radius accounting port 1813 contributes to network management by enabling the collection and storage of detailed information about user sessions, which can be used for billing, network usage tracking, and security audits.
What security measures can be taken to protect Radius server ports?
+To protect Radius server ports, security measures such as using secure protocols, configuring firewalls to restrict access, implementing rate limiting, and regularly updating Radius server software can be taken.
Meta Description: “Discover the importance of Radius server port numbers, including ports 1812 and 1813, and learn how to configure them securely for reliable network operations.”



