6 Ways IPv6 Tunnels IPv4

The transition from IPv4 to IPv6 has been a gradual process, with various mechanisms developed to facilitate the coexistence of both protocols. One such mechanism is IPv6 tunneling over IPv4 networks, which allows IPv6 packets to be encapsulated within IPv4 packets, enabling communication between IPv6 devices over an IPv4 infrastructure. This article will delve into the specifics of how IPv6 tunnels IPv4, exploring the technical aspects, benefits, and applications of this technology.
Introduction to IPv6 Tunneling
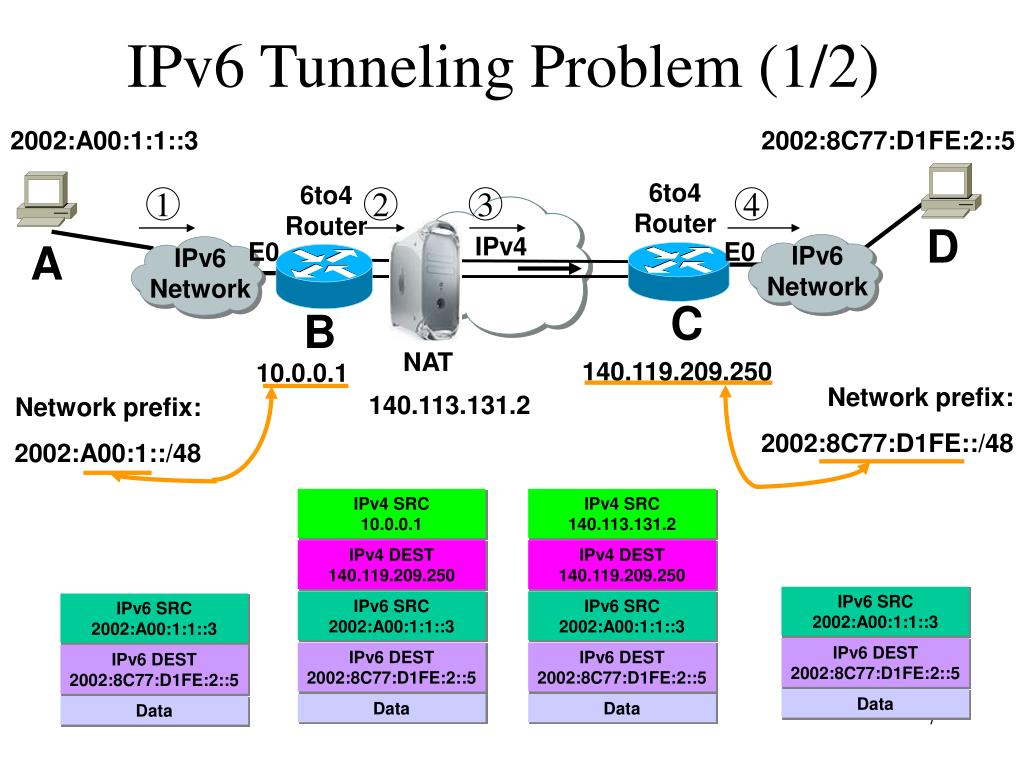
IPv6 tunneling is a technique used to transport IPv6 packets over an IPv4 network. This is particularly useful in scenarios where IPv6 connectivity is not natively supported, such as in legacy networks or during the transition phase from IPv4 to IPv6. By encapsulating IPv6 packets within IPv4 packets, devices can communicate using IPv6 even if the underlying network does not support it. This method ensures backward compatibility and facilitates a smoother transition to IPv6.
Types of IPv6 Tunneling
There are several types of IPv6 tunneling mechanisms, each designed to address specific requirements and scenarios. These include manual tunnels, 6to4 tunnels, 6RD (IPv6 Rapid Deployment) tunnels, ISATAP (Intra-Site Automatic Tunnel Addressing Protocol) tunnels, TEREDO tunnels, and 6in4 tunnels. Each of these mechanisms has its own configuration requirements, advantages, and use cases, making them suitable for different environments and applications.
| Tunneling Mechanism | Description |
|---|---|
| Manual Tunnels | Manually configured tunnels between two endpoints, requiring explicit configuration of the tunnel endpoints. |
| 6to4 Tunnels | Automatically create tunnels using a special type of IPv6 address that embeds the IPv4 address of the tunnel endpoint. |
| 6RD Tunnels | Similar to 6to4 but allows for more flexibility and easier deployment within ISP networks. |
| ISATAP Tunnels | Designed for intra-site tunneling, allowing IPv6 hosts within an IPv4 site to communicate with each other and with IPv6 hosts on other sites. |
| TEREDO Tunnels | Allows IPv6 traffic to be transmitted over UDP, facilitating IPv6 connectivity from behind NAT devices. |
| 6in4 Tunnels | A generic term for IPv6-in-IPv4 tunneling, often used in various contexts and configurations. |

Benefits and Applications of IPv6 Tunneling

IPv6 tunneling offers several benefits, including the ability to deploy IPv6 services without requiring an immediate upgrade of the underlying IPv4 infrastructure. This allows for a gradual transition, reducing costs and minimizing disruptions. Additionally, tunneling enables the coexistence of IPv4 and IPv6, facilitating communication between devices using different protocols. This technology is particularly useful in environments where IPv6 adoption is partial or where legacy systems need to interoperate with newer, IPv6-capable devices.
Challenges and Limitations
Despite its advantages, IPv6 tunneling also presents several challenges and limitations. These include increased complexity due to the additional layer of encapsulation, potential performance impacts due to the overhead of tunneling, and security concerns related to the tunneling process itself. Furthermore, the management and troubleshooting of tunnels can be more complex than native IPv6 or IPv4 configurations. Therefore, careful planning, configuration, and monitoring are necessary when implementing IPv6 tunneling solutions.
Key Points
- IPv6 tunneling is a critical mechanism for facilitating the transition from IPv4 to IPv6, enabling IPv6 communication over IPv4 networks.
- There are various types of IPv6 tunneling mechanisms, each with its own strengths and use cases.
- The benefits of IPv6 tunneling include gradual transition, coexistence of protocols, and reduced costs.
- Challenges and limitations include increased complexity, potential performance impacts, and security concerns.
- Understanding the different tunneling mechanisms and their applications is essential for effective deployment and management.
Technical Aspects and Configuration
The technical aspects of IPv6 tunneling involve the encapsulation of IPv6 packets within IPv4 packets, which requires specific configurations on the tunnel endpoints. This includes setting up the tunnel interface, configuring the IPv6 and IPv4 addresses, and ensuring that the routing tables are correctly updated to reflect the tunnel. The configuration process can vary significantly depending on the type of tunneling mechanism used and the network environment.
Security Considerations
Security is a critical aspect of IPv6 tunneling, as the tunneling process can introduce additional vulnerabilities. These include the potential for unauthorized access to the tunnel, data integrity issues due to the encapsulation process, and the increased complexity of security monitoring and management. To mitigate these risks, it is essential to implement robust security measures, such as encryption, authentication, and access control, and to regularly monitor the tunnel for any signs of compromise or malfunction.
| Security Measure | Description |
|---|---|
| Encryption | Protects the confidentiality and integrity of data transmitted through the tunnel. |
| Authentication | Ensures that only authorized devices can establish and use the tunnel. |
| Access Control | Restricts access to the tunnel based on predefined policies and user identities. |
| Monitoring | Regularly checks the tunnel for security breaches, performance issues, and configuration errors. |
Conclusion and Future Directions
In conclusion, IPv6 tunneling is a vital technology for the transition from IPv4 to IPv6, offering a flexible and gradual approach to deploying IPv6 services over existing IPv4 infrastructures. Understanding the different types of tunneling mechanisms, their benefits, and their limitations is essential for effective deployment and management. As the adoption of IPv6 continues to grow, the role of tunneling will evolve, with a focus on securing the transition process and ensuring seamless communication between devices using different protocols.
What is the primary purpose of IPv6 tunneling?
+The primary purpose of IPv6 tunneling is to enable IPv6 communication over an IPv4 network, facilitating the transition from IPv4 to IPv6.
What are the main types of IPv6 tunneling mechanisms?
+The main types of IPv6 tunneling mechanisms include manual tunnels, 6to4 tunnels, 6RD tunnels, ISATAP tunnels, TEREDO tunnels, and 6in4 tunnels, each with its own configuration requirements and use cases.
What are the benefits of using IPv6 tunneling?
+The benefits of using IPv6 tunneling include the ability to deploy IPv6 services without requiring an immediate upgrade of the underlying IPv4 infrastructure, facilitating a gradual transition and reducing costs.
What are the security considerations for IPv6 tunneling?
+Security considerations for IPv6 tunneling include the potential for unauthorized access, data integrity issues, and increased complexity of security monitoring and management, which can be mitigated through the implementation of robust security measures such as encryption, authentication, and access control.
How does IPv6 tunneling impact network performance?
+IPv6 tunneling can impact network performance due to the additional overhead of encapsulation, which can lead to increased latency and decreased throughput, although the extent of the impact depends on the specific tunneling mechanism and network environment.
What is the future of IPv6 tunneling in the context of IPv6 adoption?
+As IPv6 adoption continues to grow, the role of tunneling will evolve, with a focus on securing the transition process and ensuring seamless communication between devices using different protocols, eventually reducing the need for tunneling as native IPv6 support becomes more widespread.