What is TACACS

TACACS, which stands for Terminal Access-Control Access-Control System, is a protocol used for remote access authentication, authorization, and accounting (AAA) in computer networks. It was initially developed in the 1980s by the Department of Defense's Advanced Research Projects Agency (ARPA) and has since become a widely adopted standard in the networking industry.
Key Components of TACACS

TACACS consists of three primary components: authentication, authorization, and accounting. These components work together to provide a comprehensive AAA solution for network administrators.
Authentication
Authentication is the process of verifying the identity of users attempting to access a network or device. TACACS uses a variety of authentication methods, including username and password, challenge-response, and Kerberos. The authentication process typically involves a client-server architecture, where the client (usually a network device) sends an authentication request to the TACACS server, which then verifies the user’s credentials and responds with an authentication success or failure message.
Authorization
Authorization is the process of determining what actions a user is allowed to perform on a network or device. TACACS authorization involves checking the user’s permissions and access rights, which are typically stored in a database or directory service. The TACACS server compares the user’s identity and permissions to the requested action and responds with an authorization success or failure message.
Accounting
Accounting is the process of tracking and logging user activity on a network or device. TACACS accounting involves collecting and storing information about user sessions, including login and logout times, commands executed, and resources accessed. This information can be used for auditing, billing, and capacity planning purposes.
| Component | Description |
|---|---|
| Authentication | Verifies user identity |
| Authorization | Determines user permissions |
| Accounting | Tracks and logs user activity |

TACACS Protocols
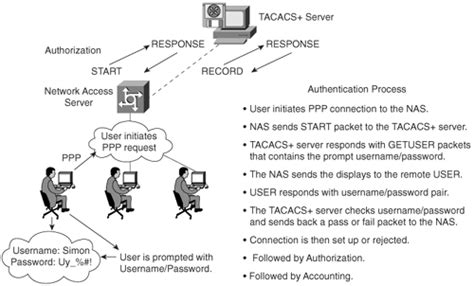
There are several TACACS protocols, including TACACS+, XTACACS, and TACACS++. TACACS+ is the most widely used protocol and is an extension of the original TACACS protocol. It provides improved security, scalability, and flexibility compared to the original protocol.
TACACS+
TACACS+ is a proprietary protocol developed by Cisco Systems. It uses a client-server architecture and provides a flexible and scalable AAA solution for network administrators. TACACS+ supports a wide range of authentication methods, including username and password, challenge-response, and Kerberos.
XTACACS
XTACACS is an extension of the original TACACS protocol. It provides improved security and scalability compared to the original protocol and is used in some legacy systems.
TACACS++
TACACS++ is a newer protocol that provides improved security and scalability compared to TACACS+. It is designed to work with modern network devices and provides support for advanced authentication methods, such as public key infrastructure (PKI) and smart cards.
Key Points
- TACACS is a protocol used for remote access AAA in computer networks.
- TACACS consists of three primary components: authentication, authorization, and accounting.
- TACACS+ is the most widely used TACACS protocol and provides improved security, scalability, and flexibility.
- TACACS is often used in conjunction with other protocols, such as RADIUS, to provide a comprehensive AAA solution.
- TACACS protocols include TACACS+, XTACACS, and TACACS++.
Advantages and Disadvantages of TACACS
TACACS provides several advantages, including improved security, scalability, and flexibility. However, it also has some disadvantages, such as complexity and compatibility issues.
Advantages
TACACS provides several advantages, including:
- Improved security: TACACS provides a secure AAA solution for network administrators, using encryption and secure authentication methods.
- Scalability: TACACS is designed to work with large networks and provides a flexible and scalable AAA solution.
- Flexibility: TACACS supports a wide range of authentication methods and provides a flexible AAA solution for network administrators.
Disadvantages
TACACS also has some disadvantages, including:
- Complexity: TACACS can be complex to configure and manage, especially for large networks.
- Compatibility issues: TACACS may not be compatible with all network devices and systems, which can cause compatibility issues.
What is TACACS used for?
+TACACS is used for remote access AAA in computer networks, providing a secure and scalable solution for network administrators.
What are the different TACACS protocols?
+The different TACACS protocols include TACACS+, XTACACS, and TACACS++.
What are the advantages of TACACS?
+TACACS provides improved security, scalability, and flexibility, making it a popular choice for network administrators.
In conclusion, TACACS is a widely used protocol for remote access AAA in computer networks. It provides a secure and scalable solution for network administrators, using a flexible and extensible architecture. While TACACS has some disadvantages, such as complexity and compatibility issues, its advantages make it a popular choice for many organizations.



